Four steps to protect your dental practice from ransomware attacks – Educate, Filter, Protect, and Backup
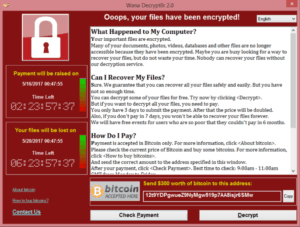
Ransomware attacks are vicious and can be extremely damaging to your day-to-day operations, your reputation, and your finances. The NHS amongst other businesses was hit recently with a ransomware known as WannaCry, Wanna Decryptor, Wanna Cryptor, WanaCrypt0r or WCry and has spread quickly around the world infecting Windows systems. The current outbreak is version 2.0 of the ransomware which was first detected on 12th May.
But just what is it? And more importantly, what can you do to stop it?
Security specialists TrendMicro explain ransomware as: “A type of malware that prevents or limits users from accessing their system, either by locking the system’s screen or by locking the users’ files unless a ransom is paid. More modern ransomware families, collectively categorized as crypto-ransomware, encrypt certain file types on infected systems and forces users to pay the ransom through certain online payment methods to get a decrypt key.”
Or in short, ransomware is a type of malicious software, designed to block access to your computer system until a sum of money is paid.
Worryingly, with ransomware, it’s not always obvious that you’ve been infected. Very often it will lie dormant before suddenly wiping your files and leaving them unrecoverable (which is why backup is so important!). And if that wasn’t bad enough; ransomware will also scour your network looking for any open shares; and, once found, do the same to any files there. So, it’s important to make sure that your server machine is as locked down as soon as possible following an attack, and wherever possible, shares should be hidden or inaccessible without the correct credentials.
But, with some Practice Management Software packages – such as Exact (SOE), R4, iSmile etc – requiring an open share on the server, just how do you avoid the security risk with ransomware, and in general?
At Just Tech, we’ve found that the threat of ransomware is best combatted by a four-stage approach.
- Educate. Train your staff to be on the lookout for any suspicious emails and to delete anything they are slightly unsure of. Get them to try out this handy little test to see how they get on!
- Filter. Email is the most common way that ransomware gets into your computers and network. Make sure you use a business class email system that filters out viruses BEFORE they hit your users’ inboxes. Hosted Exchange with Email Security, Gmail, Office 365 are all good examples of this, and, as a rule, email provided through your web company (as opposed to a specialist email service) won’t have the same level of security and filtering.
- Protect. Prevention is always better than cure so install business-class antivirus/malware that offers ACTIVE protection against ransomware attacks. This is something we do as a standard for our contract clients. Microsoft Security Essentials, along with the free versions of AVG and Avast just don’t offer the same level of protection
- Backup. We can’t stress this one enough. Backup, Backup, Backup! If you get hit by a ransomware attack the only other way to get your data back – other than paying a costly and frustrating bitcoin ransom – is to recover your data is from a backup. And, you need to make sure that your backup procedures are up to the job. Do you get backup reports daily? Do you know what is being backed up? When is your data backed up, who tests the backup, and do you know how to recover data? As a practice owner or the person responsible for data security in your practice, you need to know the answer to these questions.
Ultimately, ransomware might sound scary – and yes, it is nasty and the effects can be devastating – but it doesn’t have to be. With the right measures in place, you can minimise the risk.
Of course, even when you do follow all the right steps; an attack can still happen. New variants of ransomware are emerging all the time (just like new strains of the flu!) and, unfortunately, the people writing the viruses are usually one step ahead of the people doing the blocking. However, by following our four-step-process, you can reduce the impact on your practice should the worst happen.
When you’re running a business, the last thing you want to think about is the possibility of something going wrong. But as with most things, preparation is key. Sometimes, it pays to think the unthinkable.
An article by Matthew Bullock at Just Tech IT, your number one Dental IT support and solution provider. If you would like to get more information on how to protect your dental IT systems from hackers and ransomware then contact Matthew on 0161 298 8989. or via email info@just-tech.co.uk